About Us
Trust and Security in eKYC. We're dedicated to safeguarding your identity, making online interactions safer.

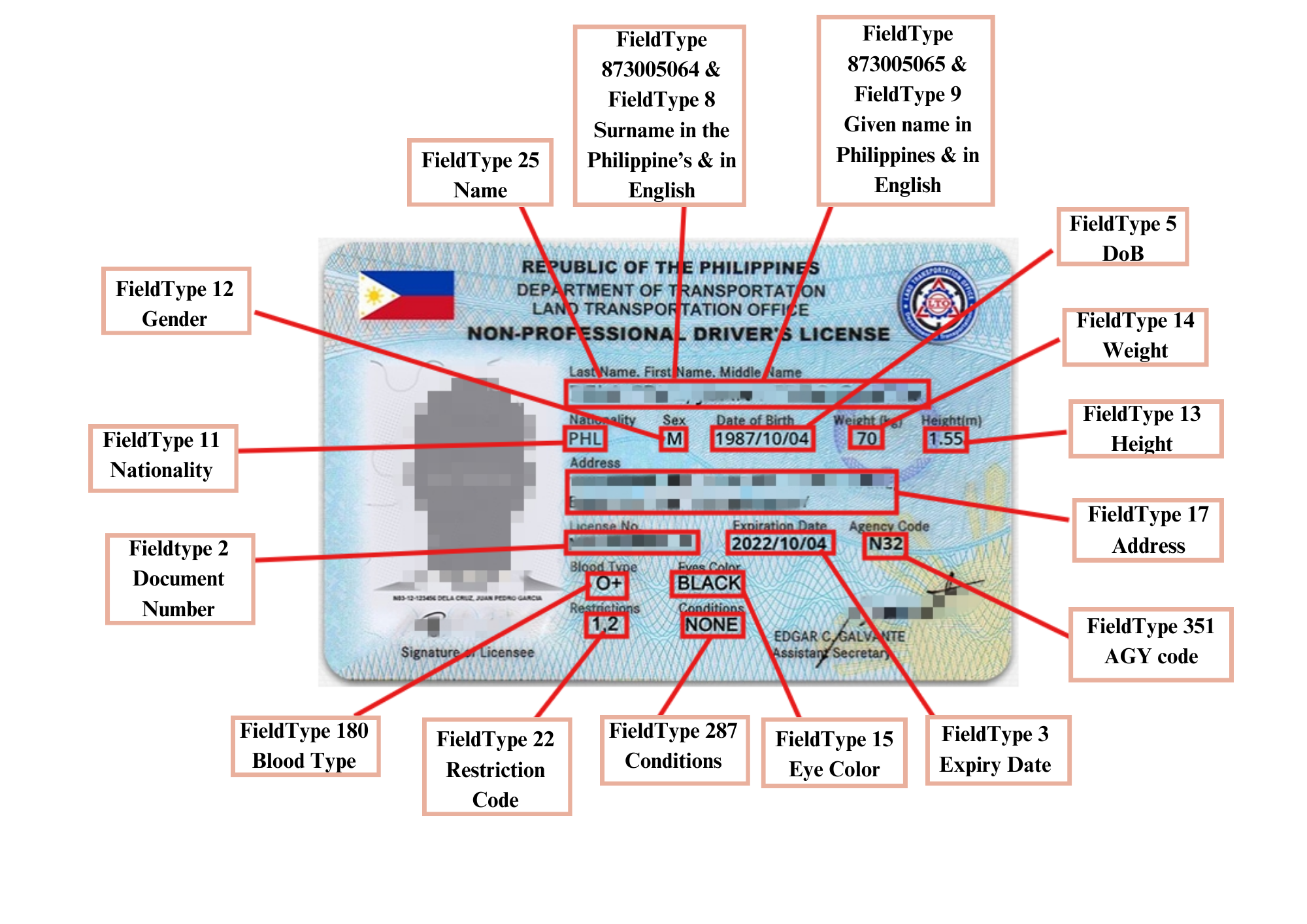
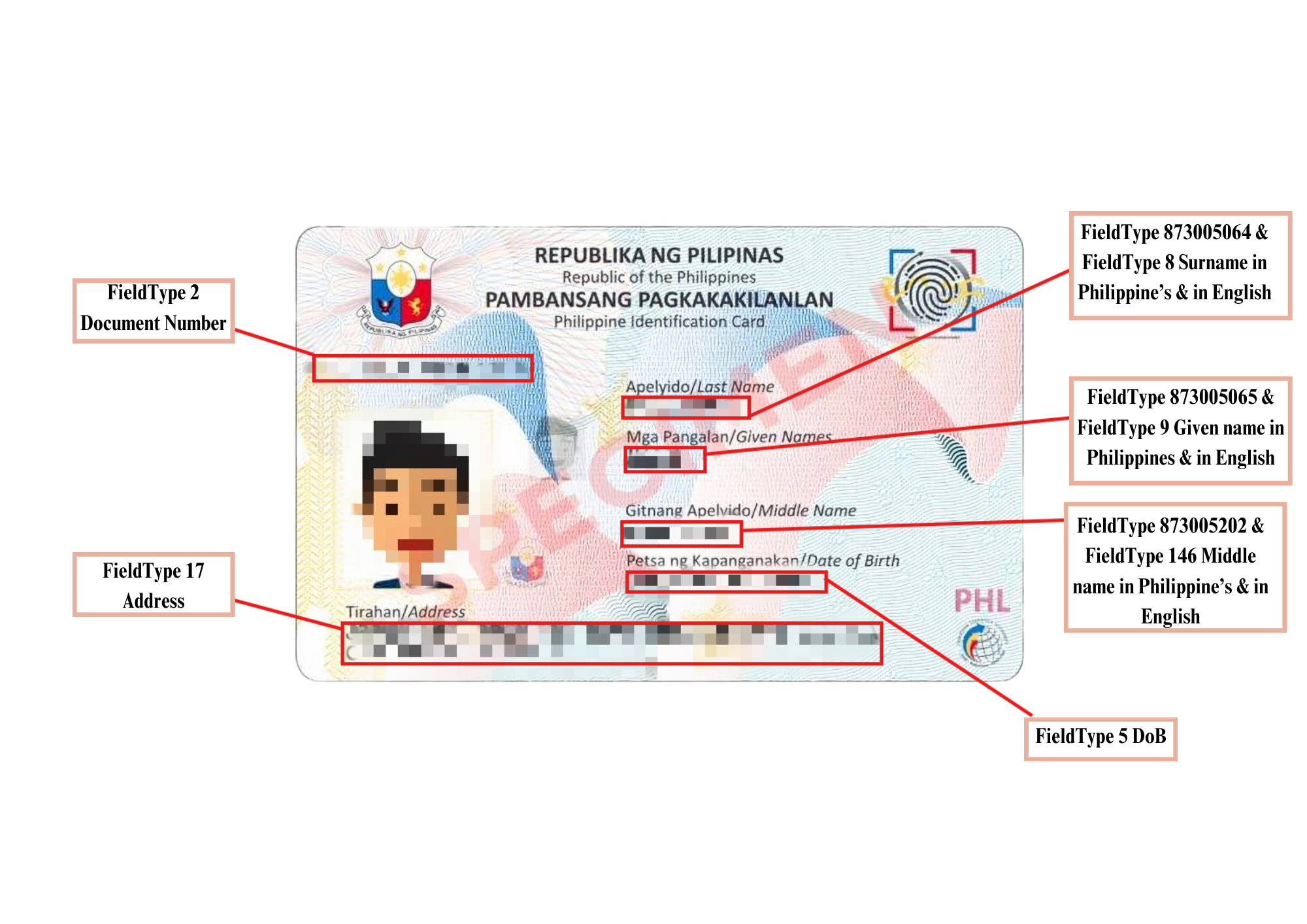
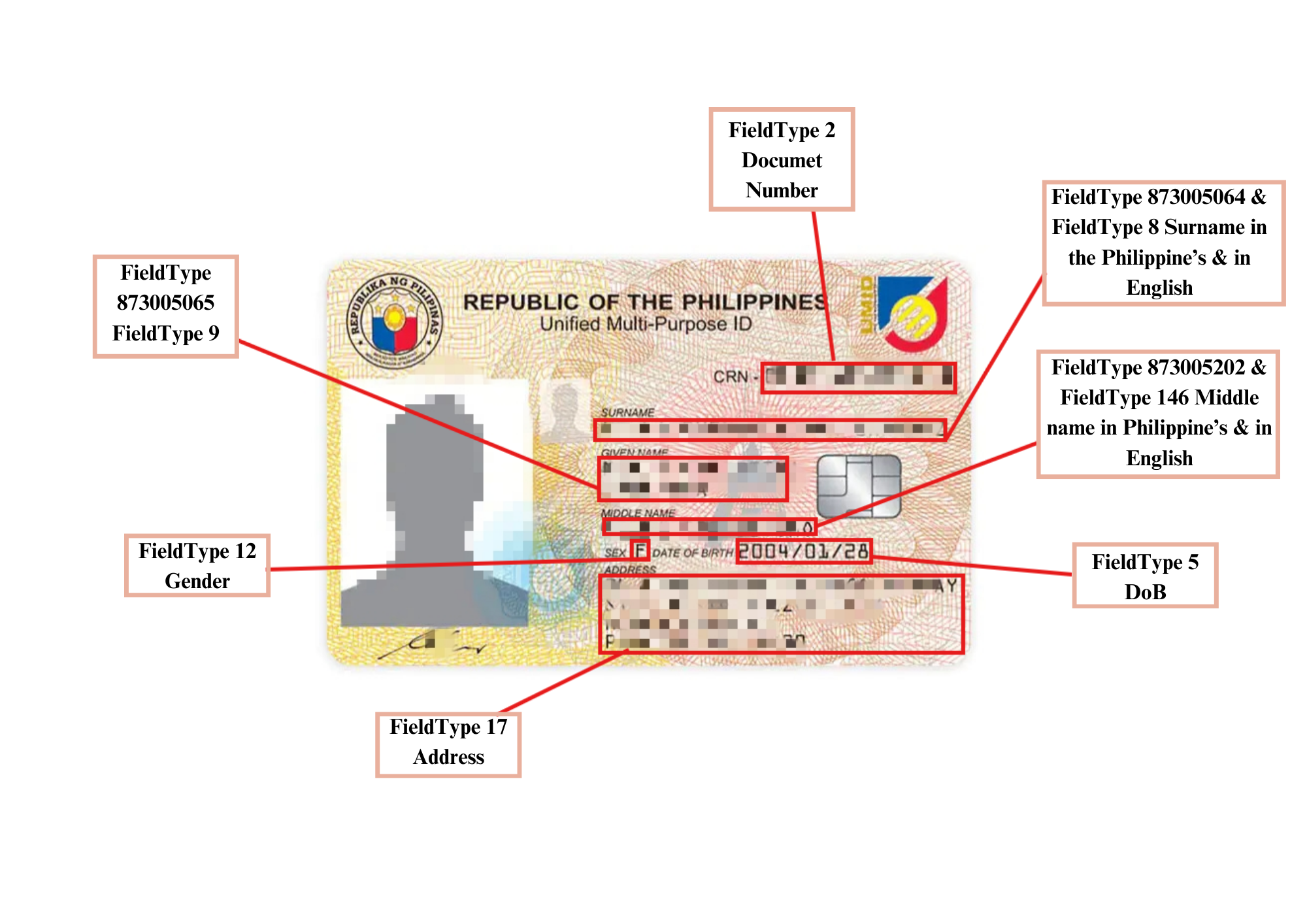
ID Document Data Extraction - OCR
Veryfy Global API recognizes Philippine IDs




Product Description
OCR And Document Verification
Capture identity card and process with computerized Al
Capture identity card and process with computerized Al
Document Verification
Landmarks are being detected by the solution, including optional microprint, position, pattern and hologram.
Bio Match And Liveliness Check
Facial Recognition Threshold
- Four seconds video is checked for liveness
- Video is analyzed for spoofing
- Facial comparison to document (%)
Face Verification Level
Default setting 70%
Risk-Based Refinement
Internally refined after further testing and determining organization's risk appetite
FAR and FRR Thresholds
FAR (False Acceptance Rate) and FRR (False Rejection Rate) to be maintained within 5%
Veryfy Global Bio-Match Check
Document Verification And Biometric Facial Recognition

Aging
Our system incorporates sophisticated algorithms to account for natural aging processes, including changes in skin texture, wrinkles, and facial contours. This ensures consistent recognition despite the passage of time.

Weight Gain/Loss
Significant fluctuations in weight can alter facial features. Our advanced facial recognition software intelligently adjusts to variations in face structure, maintaining precise identification even through physical transformations.

Plastic Surgery
Our system seamlessly adapts to updated facial profiles. It accommodates changes in nose shape, jawline, and other features with unparalleled accuracy.
e-KYC
Electronic Know Your Customer (e-KYC) is a digital process to verify the identity of customers. It uses electronic documents and online verification methods to simplify and expedite the KYC process, ensuring compliance with regulatory requirements.
Customer Onboarding
Customer Onboarding refers to the process of welcoming new customers and helping them get started with a company's products or services. This can include setting up accounts, providing necessary information, and ensuring a smooth transition into using the services offered.

Bank Account Opening
This process involves creating a new bank account for customers. It typically includes verifying personal details, gathering necessary documentation, and ensuring compliance with banking regulations to successfully open and activate the account.

Sim Card Registration
Sim Card Registration involves the process of recording the personal details of a mobile phone user when they purchase a new SIM card. This is often required by law to ensure that mobile users can be identified and to prevent misuse of mobile services.
Employee Registration
Employee Registration is the process of recording and verifying the personal and professional details of new employees. This includes collecting necessary documents, completing forms, and ensuring all legal and organizational requirements are met.

Driver's License Registration
This process involves the application and registration for obtaining a driver's license. It includes verifying the applicant's identity, ensuring they meet the necessary requirements, and processing their application for a valid driver's license.

eVisa Issuance
eVisa Issuance refers to the process of applying for and obtaining an electronic visa. This digital process simplifies the traditional visa application procedure by allowing applicants to submit their details and receive their visa online.

Digital ID Issuance
Digital ID Issuance involves creating and distributing electronic identification documents. These digital IDs are used to verify a person's identity online and are often more secure and convenient than traditional physical ID cards.

Secure
The implementation of security measures to protect data and ensure privacy. It involves using technologies and processes that safeguard information from unauthorized access, breaches, and other security threats.